Microsoft Releases Critical Recovery Tool for Windows Devices
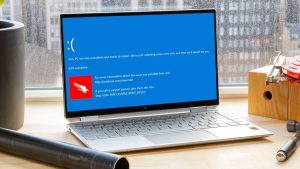
The world of information technology witnessed a major scare last week when a faulty update from a popular security solution, CrowdStrike Falcon, triggered widespread Blue Screen of Death (BSOD) errors on an estimated 8.5 million Windows devices globally. This critical system crash impacted businesses of all sizes, causing disruptions at airports, hospitals, banks, and even emergency hotlines.
The incident serves as a stark reminder of the domino effect that software updates, particularly those for security software, can have on critical infrastructure. However, it also highlights the swift action taken by Microsoft to mitigate the damage and restore normalcy.
This article delves deeper into the CrowdStrike update fiasco, the impact it had, and the recovery efforts spearheaded by Microsoft.
A Security Update Gone Wrong: How CrowdStrike Caused System Crashes
CrowdStrike Falcon is a widely used endpoint protection platform that safeguards businesses from cyber threats. On [Date of update], CrowdStrike released a routine update intended to enhance system security. Unfortunately, the update contained a critical bug that caused the software to malfunction at the kernel level.
The kernel, also known as the “core” of the operating system, manages essential system functions like memory allocation, process execution, and device drivers. Security software like CrowdStrike operates at this critical level to monitor and intercept potential threats before they can harm the system. However, when the CrowdStrike update malfunctioned, it essentially disrupted the core functionalities of the operating system, leading to system crashes and BSOD errors.
Millions Impacted: A Widespread System Outage
The faulty CrowdStrike update triggered a domino effect, rendering millions of Windows devices inoperable. Businesses of all sizes, from small stores to large corporations, felt the repercussions. Here are some of the reported disruptions:
- Transportation: Airports faced delays and cancellations due to inoperable check-in systems and other critical infrastructure.
- Healthcare: Hospitals experienced difficulties accessing patient records and managing medical equipment.
- Financial Services: Banks and financial institutions struggled to process transactions efficiently.
- Emergency Services: Disruptions were reported in some emergency hotlines, potentially hindering response times.
This widespread outage highlights the growing reliance on technology across various sectors. When a critical system like Windows encounters a security software malfunction at such a deep level, the consequences can be severe and far-reaching.
Microsoft Steps in with a Recovery Tool: Restoring Functionality
Recognizing the urgency of the situation, Microsoft swiftly developed and released a recovery tool to help IT professionals restore affected Windows machines. This downloadable tool offered a much-needed solution to the manual troubleshooting methods that would have been incredibly time-consuming and resource-intensive for large deployments.
Here’s how the Microsoft recovery tool works:
- Bootable USB Drive Creation: IT admins download the tool and use it to create a bootable USB drive.
- Accessing Affected Machines: The bootable USB drive allows access to affected machines, even if they’re unable to boot normally.
- Automatic File Removal: Once access is established, the tool automatically identifies and removes the problematic CrowdStrike file.
- System Reboot: With the faulty file removed, the system can reboot normally, restoring functionality to the affected device.
This automated approach significantly streamlined the recovery process, allowing IT teams to address a large number of machines quickly and efficiently.
Recovery Efforts and Looking Forward
While the Microsoft recovery tool provided a sigh of relief for many, the aftermath of the CrowdStrike update is still unfolding. IT departments worldwide continue to work diligently to restore operations and identify any lingering issues across their networks.
Here are some additional resources from Microsoft to aid in the recovery process:
- Recovery Instructions for Windows Virtual Machines (Link to Microsoft article)
- General Troubleshooting Steps for Windows 10 and 11 Machines (Link to Microsoft article)
Key Takeaways: Lessons Learned from the CrowdStrike Fiasco
The CrowdStrike update incident serves as a valuable learning experience for businesses and software developers alike. Here are some key takeaways:
- Rigorous Testing is Crucial: This incident highlights the importance of rigorous testing during software development and especially for security software that operates at the kernel level. Even minor bugs in such software can have devastating consequences.
- Disaster Recovery Plans are Essential: Businesses should have robust disaster recovery plans in place to minimize downtime and ensure operational continuity during unexpected IT security incidents. Regularly reviewing and updating these plans is critical.
- Communication is Key: Clear and timely communication with stakeholders during a widespread outage is essential. Businesses should have a communication strategy in place to keep employees, customers, and partners informed of the situation and potential delays.
FAQs
Q: What caused the widespread system crashes on Windows devices?
A: The issue stemmed from a faulty update released by CrowdStrike Falcon, a popular endpoint protection platform. The update contained a bug that caused the software to malfunction at the kernel level, leading to Blue Screen of Death (BSOD) errors and system crashes.
Q: How many devices were affected by the CrowdStrike update?
A: Estimates suggest that approximately 8.5 million Windows devices globally were impacted by the faulty update.
Q: What kind of businesses were affected by the outage?
A: Businesses of all sizes, including airports, hospitals, banks, financial institutions, emergency hotlines, and even small stores experienced disruptions due to the widespread system crashes.
Q: How did Microsoft address the issue?
A: Microsoft released a downloadable recovery tool that IT professionals could use to create a bootable USB drive. This USB drive allowed them to access affected machines, even in a non-bootable state, and automatically remove the problematic CrowdStrike file, restoring functionality to the device.
Q: Where can I find additional information on the recovery process?
A: Microsoft has released separate resources for recovery instructions specific to Windows Virtual Machines and general troubleshooting steps for Windows 10 and 11 machines. Links to these resources can be found in the “Recovery Efforts and Looking Forward” section of this article.
Q: What are some key takeaways from this incident?
A: This incident highlights the importance of rigorous testing for software updates, especially for security software that operates at the kernel level. Additionally, it emphasizes the need for robust disaster recovery plans and clear communication strategies for businesses to navigate unexpected IT security issues.