The Windows Defender Security Warning: Protecting Your System with Confidence
In today’s digital age, computer security has become of utmost importance. With the increasing prevalence of cyber threats, it is crucial to protect our systems from potential harm. Windows Defender, a built-in security feature in Windows operating systems, plays a vital role in safeguarding our computers.
However, users often encounter the Windows Defender Security Warning, which can be confusing and alarming. The purpose of this article is to provide comprehensive information and guidance on understanding and addressing this security warning, allowing users to protect their systems with confidence.
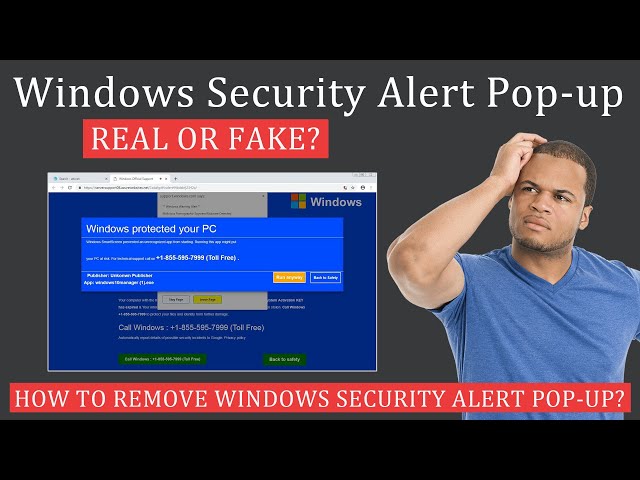
Understanding the Windows Defender Security Warning
What is the Windows Defender Security Warning?
The Windows Defender Security Warning is a notification generated by Windows Defender when it detects a potential security threat on your system. It serves as an alert to inform users about potential risks and allows them to take appropriate actions to mitigate them.
Various scenarios can trigger the warning, such as the detection of malware, suspicious files, or potentially unwanted programs. It is essential to pay attention to these warnings as they indicate potential risks to your system’s security.
How Does Windows Defender Identify Security Threats?
Windows Defender employs various mechanisms to identify security threats to your system. One of its primary methods is real-time scanning, where it continuously monitors files and processes for any suspicious activities or known malware signatures.
Additionally, Windows Defender utilizes behavioral analysis to detect potential threats. It analyzes the behavior of programs and processes, looking for patterns that indicate malicious intent.
Keeping Windows Defender definitions up to date is crucial, as these definitions contain the latest information about known threats. Regular updates ensure that Windows Defender can effectively identify and protect against the latest security risks.
Different Types of Windows Defender Security Warnings
Windows Defender Security Warnings come in various forms, each indicating a specific type of threat or risk. These warning messages provide valuable information about the nature of the detected issue. It is essential to understand these different types to respond appropriately.
Examples of common warning messages include “Malware Detected,” “Suspicious File,” or “Potentially Unwanted Program.” Each message implies a different level of severity and requires a tailored response.
Understanding the Severity Levels of the Warnings
Windows Defender Security Warnings are assigned different severity levels based on the potential impact and risk they pose to your system. It is important to understand these severity levels to prioritize your response and take appropriate action.
Severity levels can range from low to high, with low-level warnings indicating a minimal risk and high-level warnings indicating a significant threat. The severity level determines the urgency and intensity of the actions you need to take.
When you receive a warning, it is crucial to assess the severity level and consider the potential consequences for your system’s security and performance. This will help you determine the appropriate steps to protect your system.
Responding to the Windows Defender Security Warning
Initial Steps When Receiving a Warning
When you receive a Windows Defender Security Warning, it is important to take immediate action. However, it is also crucial to approach the situation calmly and avoid panic. Here are the initial steps to follow when receiving a warning:
Read the warning message carefully and make sure to understand the nature of the threat.
Verify the legitimacy of the warning message by checking if it comes from Windows Defender and not a fake or malicious source.
Take note of the severity level assigned to the warning, as it will help determine the urgency of your response.
Analyzing and Assessing the Threat
Once you have taken the initial steps, it is important to analyze and assess the detected threat to determine the appropriate course of action. Follow these steps to effectively analyze and assess the threat:
Investigate the detected threat by gathering additional information. Use Windows Defender tools such as the Threat History or the Windows Security app to gain more insights into the threat.
Consider the potential impact and scope of the threat. Evaluate whether it is a standalone issue or part of a larger security breach.
Assess the level of risk the threat poses to your system and sensitive data. This will help you prioritize your response and allocate resources accordingly.
Taking Action: Cleaning, Quarantining, or Ignoring
Based on your analysis and assessment of the threat, you can take appropriate action to protect your system. Here are the different actions you can consider:
Cleaning and removing the threat: If the threat is confirmed and poses a significant risk, use Windows Defender to clean and remove the malicious files or programs.
Quarantining suspicious files: In some cases, it may be necessary to quarantine suspicious files for further analysis. This can help prevent the threat from spreading while you investigate its nature.
Ignoring certain warnings: Not all warnings may indicate a genuine threat. If you have verified that a warning is a false positive or does not pose a significant risk, you can choose to ignore it. However, exercise caution and ensure proper verification before ignoring any warning.
Preventive Measures and Strengthening Security
Responding to Windows Defender Security Warnings is essential, but it is equally important to take preventive measures to strengthen your system’s overall security. Consider the following steps:
Enhance system security: Implement best practices such as using strong and unique passwords, enabling firewall protection, and practicing safe browsing habits.
Regular system updates and patches: Keep your operating system and applications up to date with the latest security patches. This helps protect against known vulnerabilities that can be exploited by attackers.
Utilize additional security software: While Windows Defender provides robust protection, using additional security software can add an extra layer of defense. Consider using reputable antivirus and anti-malware software to complement Windows Defender.
Frequently Asked Questions
How can I update Windows Defender definitions?
To update Windows Defender definitions, follow these steps:
Open Windows Security by clicking on the shield icon in the taskbar or searching for “Windows Security” in the Start menu.
Go to “Virus & threat protection” and click on “Check for updates” under the “Protection updates” section.
Windows Defender will check for updates and download the latest definitions if available.
Can I trust Windows Defender to detect all threats?
While Windows Defender is a robust security solution, no antivirus software can guarantee 100% detection of all threats. It is important to adopt a multi-layered security approach by combining Windows Defender with other security measures such as safe browsing habits and regular system updates.
How can I differentiate between a genuine threat and a false positive?
To differentiate between a genuine threat and a false positive, consider the following steps:
Verify the source of the warning message to ensure it is legitimate and not a fake or malicious notification.
Investigate the detected threat further using Windows Defender tools or other reputable antivirus software.
Compare the warning message with known indicators of genuine threats to determine if it aligns with typical behavior.
If in doubt, seek assistance from cybersecurity professionals or report the potential false positive to Microsoft.
What should I do if Windows Defender blocks a legitimate program?
If Windows Defender blocks a legitimate program, you can follow these troubleshooting steps:
Open Windows Security and go to “Virus & threat protection.”
Under “3.4 What should I do if Windows Defender blocks a legitimate program?
If Windows Defender blocks a legitimate program, you can follow these troubleshooting steps:
Open Windows Security and go to “Virus & threat protection.”
Under “Virus & threat protection settings,” click on “Manage settings.”
Scroll down to the “Exclusions” section and click on “Add or remove exclusions.”
Click on “Add an exclusion” and choose the type of exclusion you want to add (file, folder, file type, or process).
Select the specific file, folder, file type, or process that Windows Defender blocked and add it as an exclusion.
Once added, Windows Defender should no longer block the legitimate program.
If the issue persists or you are unsure about the legitimacy of the program, it is recommended to seek assistance from the program’s developer or contact Microsoft support for further guidance.
Is Windows Defender enough, or should I use additional security software?
Windows Defender provides robust protection against a wide range of threats and is sufficient for many users. However, depending on your specific needs and preferences, you may choose to use additional security software alongside Windows Defender for added layers of protection.
Reputable antivirus and anti-malware software from trusted vendors can provide extra features and specialized protection. It is important to ensure that any additional software you install is compatible with Windows Defender and does not conflict with its functionality.
Ultimately, the decision to use additional security software depends on your risk tolerance and the level of security you desire for your system.
Conclusion:
Understanding and addressing the Windows Defender Security Warning is crucial for protecting your system with confidence. By comprehending the nature of the warnings, analyzing and assessing threats, and taking appropriate actions, you can effectively safeguard your computer from potential risks.
Remember to keep Windows Defender definitions up to date, practice safe browsing habits, and regularly update your system to strengthen overall security. By staying vigilant and proactive, you can protect your personal and business data from the ever-evolving landscape of cyber threats.